AWVS13.X API学习记录
AWVS 还是比较经典的,最近想用 Django 去调用 AWVS 的 API,在前辈们公开的 AWVS11 的 API 基础上,国光均一个个测试接口是否正常工作,对工作异常的接口国光也抓包来进行了分析,本文的 AWVS13 API 国光均一一验证过。
准备工作
获取 API-KEY
「Administrator」-「Profile」-「API Key」-「Generate New Api Key」
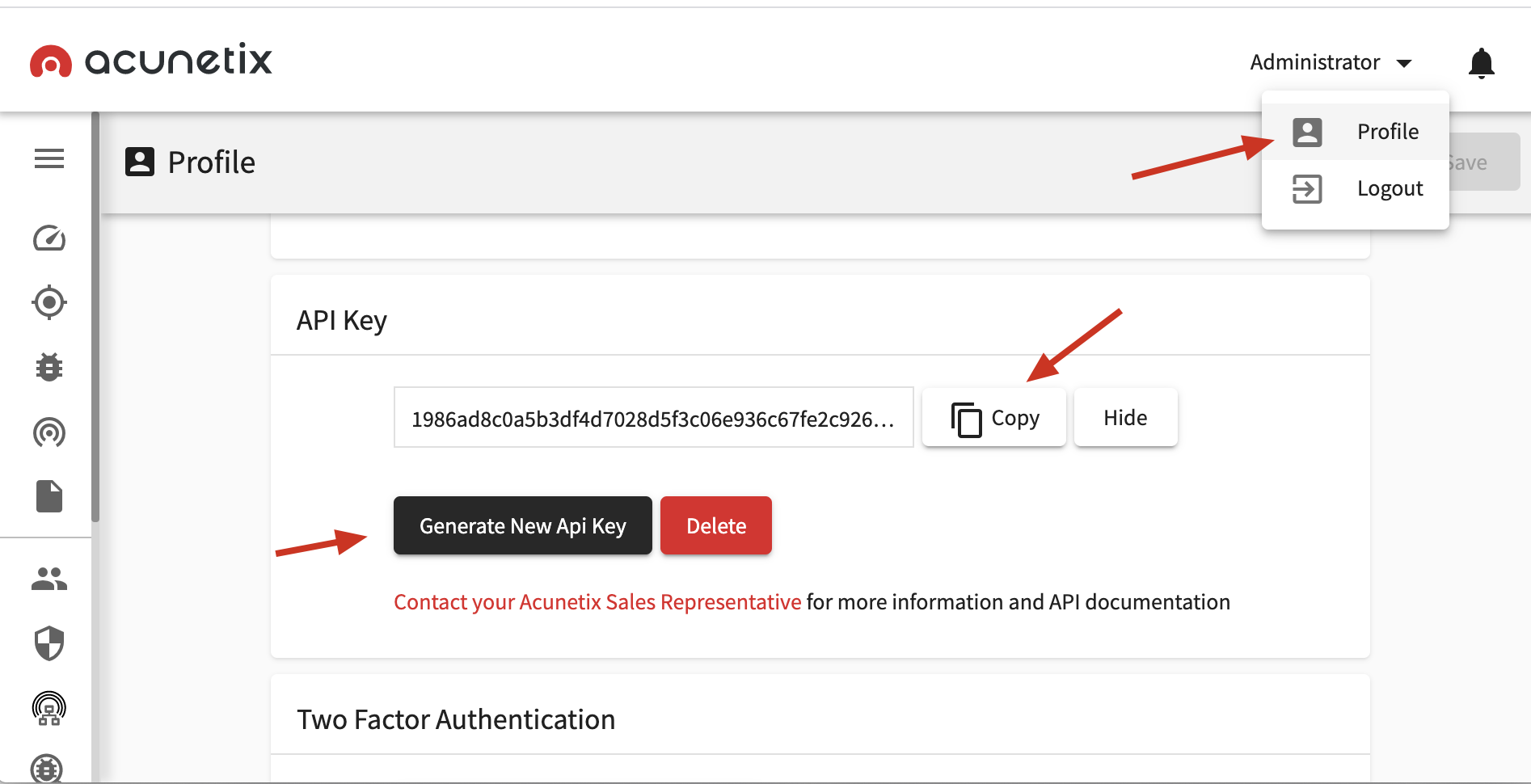
国光此时的 API Key 为:
1986ad8c0a5b3df4d7028d5f3c06e936c67fe2c92688a43729821dfd939635a01Header 设置
X-Auth: API-KEY
Content-type: application/json; charset=utf8下面分别用 curl 和 Python 的 requests 库来简单演示一下 API Key 的使用
查看账户信息的 api 是:
Method:GET
URL: /api/v1/mecurl
curl 'https://127.0.0.1:13443/api/v1/me' -H 'Content-Type: application/json;charset=utf8' -H 'X-Auth: 1986ad8c0a5b3df4d7028d5f3c06e936c67fe2c92688a43729821dfd939635a01' -k-H: 自定义 HTTP头-k: 关闭 curl 的 SSL 安全验证,跳过 SSL 检测
requests
import requests
from requests.packages.urllib3.exceptions import InsecureRequestWarning
requests.packages.urllib3.disable_warnings(InsecureRequestWarning)
api_url = 'https://127.0.0.1:13443/api/v1/info'
headers = {
'X-Auth': '1986ad8c0a5b3df4d7028d5f3c06e936c67fe2c92688a43729821dfd939635a01',
'Content-type': 'application/json'
}
r = requests.get(url=api_url, headers=headers, verify=False)
print(r.json())因为 Python 的 requests 模块会在控制台输出 SSL 不安全的警告信息,除了添加了verify=False之外,还添加了下面这两行代码,来手动关闭警告信息:
from requests.packages.urllib3.exceptions import InsecureRequestWarning
requests.packages.urllib3.disable_warnings(InsecureRequestWarning)接口设置
- 传参内容均为JSON格式
- 接口均为https
接口验证
浏览器审查元素配合AWVS的界面,再结合AWVS11的文档,基本上还是很容易上手接口的,因为文档叙述能力有限,建议大家有需求的话 自己抓包去看一下请求头和返回头,加深对AWVS13接口的理解。
Dashboard
证书信息
Method:GET
URL: /api/v1/info返回参数说明:
| 参数 | 说明 |
|---|---|
| build_number | 版本号 |
| license | 授权信息 |
| license_key | 授权信息 |
| limits | 主要版本号 |
| maintenance_expires | 小版本号 |
| major_version”: | 创建时间 |
| max_network_scan_time | 最大网络扫描时间 |
| max_web_scan_time | 最大Web扫描时间 |
| minor_version | 次版本号 |
| update_info | 更新信息 |
AWVS13接口详细返回信息:
{
"acumonitor": false,
"build_number": "200217097",
"license": {
"access": true,
"activated": true,
"email": "test@test.com",
"error": null,
"expired": false,
"expires": "false",
"features": [
"pause_resume",
"compliance_reports",
"target_business_criticality",
"network_scans",
"export_waf",
"updates",
"multi_user",
"offline_activations",
"multi_engine",
"api_key",
"target_groups",
"trending_graphs",
"vuln_retest",
"scanning_profiles",
"continuous_scans",
"bug_tracking_integration",
"acumonitor"
],
"grace_period_end": null,
"license_key": "Cracked-By-nszy007-Funning",
"limits": {
"demo_targets": 5,
"standard_targets": 999999,
"engines": 999999,
"users": null
},
"maintenance_expired": false,
"maintenance_expires": "2099-10-01T20:17:52",
"product_code": "AOPENT"
},
"licensing_extra": {
"extra_std_target_count": 0,
"extra_user_count": 0,
"can_create_new_std_target": true,
"can_create_new_demo_target": true,
"can_create_new_user": true,
"target_deletion_allowance": 2,
"unique_std_target_count": 19,
"unique_net_target_count": 0,
"user_count": 1
},
"major_version": "13",
"max_network_scan_time": 2880,
"max_web_scan_time": 2880,
"minor_version": "0",
"update_info": {
"build_number": "-",
"major_version": "12",
"minor_version": "-",
"new_update": false,
"update_status": "none"
}
}账户信息
Method:GET
URL: /api/v1/me返回参数说明:
| 参数 | 说明 |
|---|---|
| child_account | 是否子账户 |
| Email地址 | |
| enabled | 当前账户是否启用 |
| first_name | 当前账户名 |
| user_id | 当前用户id |
| totp_enabled | 是否启用toptp |
| su | 是否最高权限 |
AWVS13接口详细返回信息:
{
"child_account": false,
"email": "admin@admin.com",
"enabled": true,
"first_name": "Administrator",
"user_id": "986ad8c0-a5b3-df4d-7028-d5f3c06e936c",
"totp_enabled": false,
"su": true
}节点引擎信息
Method:GET
URL: /api/v1/workers返回参数说明:
| 参数 | 说明 |
|---|---|
| workers | 工作的节点引擎 |
| endpoint | 节点信息 |
| scanning_app | 扫描应用程序 |
| app_version | 应用程序版本信息 |
| authorization | 授权状态 |
| description | 节点引擎描述 |
| status | 节点引擎状态 |
| worker_id | 节点引擎id |
详细返回信息:
{
"workers": [
{
"endpoint": "Main Installation",
"scanning_app": "wvs",
"app_version": "13.0.200217097",
"authorization": "authorized",
"description": "Main Installation",
"status": "online",
"worker_id": "ffffffff-ffff-ffff-ffff-ffffffffffff"
}
]
}通知信息
Method:GET
URL: /api/v1/notifications返回参数说明:
| 参数 | 说明 |
|---|---|
| notifications | 通知 |
| pagination | 分页 |
AWVS13 接口详细返回信息:
{
"notifications": [
{
"consumed": false,
"created": "2020-04-13T23:44:19.592629+00:00",
"data": {
"name": "20200413_Affected_Items_http_testphp_vulnweb_com_",
"source": "http://testphp.vulnweb.com/;AWVS\u6d4b\u8bd5\u9776\u573a",
"creator": "admin@admin.com",
"source_type": "scans",
"template_name": "Affected Items",
"file_attachments": [
{
"name": "20200413_Affected_Items_http_testphp_vulnweb_com_.pdf",
"path": "/home/acunetix/.acunetix/data/reports/20822f5f-59c9-4ce1-921a-76f3ec1493f1.pdf",
"type": "file"
}
]
},
"email": null,
"notification_id": "2286746570391029408",
"resource_id": "20822f5f-59c9-4ce1-921a-76f3ec1493f1",
"resource_type": 7,
"severity": 0,
"type_id": 601,
"user_id": null
}
],
"pagination": {
"count": 1,
"cursor_hash": "d16cdad638d278c14a209a6189016393",
"cursors": [
null
],
"sort": null
}
}Dashboard 信息
Method:GET
URL: /api/v1/me/stats返回参数说明:
| 参数 | 说明 |
|---|---|
| most_vulnerable_targets | 最脆弱的目标 |
| scans_conducted_count | 总进行扫描个数 |
| scans_running_count | 正在扫描的个数 |
| scans_waiting_count | 等待扫描的个数 |
| targets_count | 总进行扫描个数 |
| top_vulnerabilities | 排名靠前漏洞分布 |
| vuln_count_by_criticality | 通过危险程度进行漏洞等级个数分布 |
| vuln_count | 漏洞数据 |
| vuln_count_by_criticality | 通过危险程度进行漏洞等级个数分布 |
| top_vulnerabilities | 排名靠前漏洞分布 |
| vulnerabilities_open_count | 共发现漏洞总数 |
AWVS13 接口详细返回信息:
{
"most_vulnerable_targets": [
{
"address": "http://testphp.vulnweb.com/",
"criticality": 10,
"high_vuln_count": 45,
"med_vuln_count": 66,
"target_id": "7b70e73f-bad0-4531-99a8-69d916ed7e66"
}
],
"scans_conducted_count": 1,
"scans_running_count": 0,
"scans_waiting_count": 0,
"targets_count": 1,
"top_vulnerabilities": [
{
"count": 21,
"name": "SQL injection",
"severity": 3,
"vt_id": "db04b846-7dec-fb62-f12d-1a152945cdae"
},
{
"count": 21,
"name": "HTML form without CSRF protection",
"severity": 2,
"vt_id": "ca3a4dd5-3f3b-4b43-527e-3210a52f9c8c"
},
{
"count": 16,
"name": "Cross site scripting",
"severity": 3,
"vt_id": "7a2fa5a4-7125-1062-0651-ed5219f05809"
},
{
"count": 14,
"name": "Directory listing",
"severity": 2,
"vt_id": "b53afc6c-83c3-7ea8-ce7b-d5f5fb01b7d7"
},
{
"count": 7,
"name": "Error message on page",
"severity": 2,
"vt_id": "d6b36f54-09ec-af8d-df8a-5f76932151ca"
},
{
"count": 4,
"name": "Application error message",
"severity": 2,
"vt_id": "760d5a01-dc58-fcbe-6c21-4f04c64a2467"
},
{
"count": 2,
"name": "Backup files",
"severity": 2,
"vt_id": "7777c336-316c-a967-2acd-45b7ee798413"
},
{
"count": 2,
"name": "Source code disclosure",
"severity": 2,
"vt_id": "61125d6e-3fdf-a73d-1c2d-1bf8a3bef84d"
},
{
"count": 2,
"name": "User credentials are sent in clear text",
"severity": 2,
"vt_id": "92a2df52-5f25-bff6-2e5b-64717a2a417e"
},
{
"count": 1,
"name": "Macromedia Dreamweaver remote database scripts",
"severity": 3,
"vt_id": "78a18edd-b1fd-7d7f-cc43-df8d6b43dba1"
}
],
"vuln_count": {
"high": 45,
"low": 10,
"med": 66
},
"vuln_count_by_criticality": {
"critical": null,
"high": null,
"low": null,
"normal": {
"high": 45,
"low": 10,
"med": 66
}
},
"vulnerabilities_open_count": 121
} Targets
所有目标信息
Method:GET
URL: /api/v1/targets返回参数说明:
| 参数 | 说明 |
|---|---|
| targets | 目标详细信息 |
| pagination | 分页信息 |
targets
| 参数 | 说明 |
|---|---|
| address | 扫描目标网址 |
| continuous_mode | 是否连续模式 |
| criticality | 危险程度 |
| description | 描述 |
| last_scan_date | 最近扫描的日期 |
| last_scan_id | 最近扫描的id |
| last_scan_session_id | 最近扫描的session id |
| last_scan_session_status | 最近的扫描状态 |
| manual_intervention | 手动干预 |
| severity_counts | 漏洞等级个数分布 |
| target_id | 目标id |
| threat | 威胁等级 |
| type | 类型 |
| verification | 验证 |
AWVS13 接口详细返回信息:
{
"targets": [
{
"address": "http://testphp.vulnweb.com/",
"continuous_mode": false,
"criticality": 10,
"description": "AWVS\u6d4b\u8bd5\u9776\u573a",
"last_scan_date": "2020-04-13T10:17:09.880580+00:00",
"last_scan_id": "506a2238-aaf2-487a-884b-b152fedffb10",
"last_scan_session_id": "21124419-2a02-458e-82bf-fabab3462ddc",
"last_scan_session_status": "completed",
"manual_intervention": null,
"severity_counts": {
"high": 45,
"info": 26,
"low": 10,
"medium": 66
},
"target_id": "7b70e73f-bad0-4531-99a8-69d916ed7e66",
"threat": 3,
"type": "demo",
"verification": "demo"
}
],
"pagination": {
"count": 1,
"cursor_hash": "8f629dd49f910b9202eb0da5d51fdb6e",
"cursors": [
null
],
"sort": null
}
}筛选目标信息
发送参数说明:
| 参数 | 类型 | 说明 |
|---|---|---|
| threat | int | 威胁等级;高->低:[3,2,1,0] |
| criticality | int | 危险程度;高->低:[30,20,10,0] |
Method:GET
URL: /api/v1/targets?q=threat:{list};criticality:{list};Demo:
curl 'https://127.0.0.1:13443/api/v1/targets?q=threat:3;criticality:10,20' -H 'Content-Type: application/json;charset=utf8' -H 'X-Auth: 1986ad8c0a5b3df4d7028d5f3c06e936c67fe2c92688a43729821dfd939635a01' -k返回内容:
{
"targets": [
{
"address": "http://testphp.vulnweb.com/",
"continuous_mode": false,
"criticality": 10,
"description": "AWVS\u6d4b\u8bd5\u9776\u573a",
"last_scan_date": "2020-04-13T10:17:09.880580+00:00",
"last_scan_id": "506a2238-aaf2-487a-884b-b152fedffb10",
"last_scan_session_id": "21124419-2a02-458e-82bf-fabab3462ddc",
"last_scan_session_status": "completed",
"manual_intervention": null,
"severity_counts": {
"high": 45,
"info": 26,
"low": 10,
"medium": 66
},
"target_id": "7b70e73f-bad0-4531-99a8-69d916ed7e66",
"threat": 3,
"type": "demo",
"verification": "demo"
}
],
"pagination": {
"count": 1,
"cursor_hash": "86f4a853c258889b8e418b3d8f493679",
"cursors": [
null
],
"sort": null
}
}添加目标
Method:POST
URL: /api/v1/targetsData:
{"address":"http://www.sqlsec.com","description":"xxxx","criticality":"10"}发送参数说明:
| 参数 | 类型 | 说明 |
|---|---|---|
| address | string | 目标网址:需http或https开头 |
| criticality | Int | 危险程度;范围:[30,20,10,0];默认为10 |
| description | string | 备注 |
返回参数说明:
| 参数 | 说明 |
|---|---|
| address | 目标网址 |
| criticality | 危险程度 |
| description | 备注 |
| type | 类型 |
| domain | 域名 |
| target_id | 目标id |
| target_type | 目标类型 |
| canonical_address | 根域名 |
| canonical_address_hash | 根域名hash |
Demo:
curl -d '{"address":"http://www.sqlsec.com","description":"xxxx","criticality":"10"}' 'https://127.0.0.1:13443/api/v1/targets' -H 'Content-Type: application/json;charset=utf8' -H 'X-Auth: 1986ad8c0a5b3df4d7028d5f3c06e936c67fe2c92688a43729821dfd939635a01' -k返回信息:
{
"address": "http://www.sqlsec.com",
"criticality": 10,
"description": "xxxx",
"type": "default",
"domain": "www.sqlsec.com",
"target_id": "28b11aa7-9c55-4a65-9cdd-70998e216af8",
"target_type": null,
"canonical_address": "sqlsec.com",
"canonical_address_hash": "bad762b4a4bf172ab58592476b6d9ee7"
}删除目标
Method:DELETE
URL: /api/v1/targets/{target_id}Demo:
curl -X DELETE 'https://127.0.0.1:13443/api/v1/targets/28b11aa7-9c55-4a65-9cdd-70998e216af8' -H 'Content-Type: application/json;charset=utf8' -H 'X-Auth: 1986ad8c0a5b3df4d7028d5f3c06e936c67fe2c92688a43729821dfd939635a01' -k无返回信息
规则设置
General 设置
criticality 设置
Method:PATCH
URL: /api/v1/targets/{target_id}Data:
{"description":"xxxx","criticality":20}发送参数说明:
| 参数 | 类型 | 说明 |
|---|---|---|
| description | String | 备注 |
| criticality | Int | 危险程度;范围:[30,20,10,0] |
Demo:
curl -X PATCH -d '{"description":"国光的测试","criticality":10}' 'https://127.0.0.1:13443/api/v1/targets/8fe7fcfd-660a-4d70-a5ae-1e599bd8ff8a' -H 'Content-Type: application/json;charset=utf8' -H 'X-Auth: 1986ad8c0a5b3df4d7028d5f3c06e936c67fe2c92688a43729821dfd939635a01' -k无返回信息
连续扫描(Continuous Scanning)
Method:POST
URL: /api/v1/targets/{target_id}/continuous_scanData:
{"enabled":false}发送参数说明:
| 参数 | 类型 | 说明 |
|---|---|---|
| enabled | bool | 关闭:false;开启:true |
Demo:
curl -d '{"enabled":true}' 'https://127.0.0.1:13443/api/v1/targets/8fe7fcfd-660a-4d70-a5ae-1e599bd8ff8a/continuous_scan' -H 'Content-Type: application/json;charset=utf8' -H 'X-Auth: 1986ad8c0a5b3df4d7028d5f3c06e936c67fe2c92688a43729821dfd939635a01' -k返回信息:
{
"enabled": false
}连续扫描:在运行完了第一次初始化扫描之后,确认并且修复了已经检测到的漏洞缺陷,并且确认目标网站没有包含漏洞和安全问题之后,需要连续扫描来确保目标站点处于安全状态。对目标url进行连续扫描,并且给予每天的的日常扫描报告是否检测到了新的安全漏洞。
扫描速度(Scan Speed)
Method:PATCH
URL: /api/v1/targets/{target_id}/configurationData:
{"scan_speed":"sequential"}发送参数说明:
| 参数 | 类型 | 说明 |
|---|---|---|
| scan_speed | string | 由慢到快:sequential slow moderate fast |
Demo:
curl -X PATCH -d '{"scan_speed":"sequential"}' 'https://127.0.0.1:13443/api/v1/targets/8fe7fcfd-660a-4d70-a5ae-1e599bd8ff8a/configuration' -H 'Content-Type: application/json;charset=utf8' -H 'X-Auth: 1986ad8c0a5b3df4d7028d5f3c06e936c67fe2c92688a43729821dfd939635a01' -k无返回信息
速度越慢扫描的也越仔细,鱼和熊掌不可兼得。
登录设置(Site Login)
Method: PATCH
URL: /api/v1/targets/{target_id}/configuration使用设定好的用户名和密码登录:
{"login":{"kind":"automatic","credentials":{"enabled":true,"username":"admin","password":"P@ssw0rd"}},"ssh_credentials":{"kind":"none"},"sensor":false}不使用站点登录:
{"login":{"kind":"none"},"ssh_credentials":{"kind":"none"},"sensor":false,}发送参数说明:
| 参数 | 类型 | 说明 |
|---|---|---|
| login | dict | 站点预设登录 |
| kind | string | 启用:automatic; 不启用:none(默认); 使用登录序列:sequence |
| credentials | dict | 登录凭证 |
| enabled | bool | false/true |
| username | string | 用户名 |
| password | string | 密码 |
| ssh_credentials | dict | SSH凭证 |
| sensor | bool | 传感器 |
Demo:
curl -X PATCH -d '{"login":{"kind":"automatic","credentials":{"enabled":true,"username":"admin","password":"P@ssw0rd"}},"ssh_credentials":{"kind":"none"},"sensor":false}' 'https://127.0.0.1:13443/api/v1/targets/8fe7fcfd-660a-4d70-a5ae-1e599bd8ff8a/configuration' -H 'Content-Type: application/json;charset=utf8' -H 'X-Auth: 1986ad8c0a5b3df4d7028d5f3c06e936c67fe2c92688a43729821dfd939635a01' -k无返回信息
Crawl 爬虫
Method:PATCH
URL: /api/v1/targets/{target_id}/configurationData:
{"user_agent":"Opera/9.80 (Windows NT 6.0; U; en) Presto/2.8.99 Version/11.10","limit_crawler_scope":true,"excluded_paths":[],
}发送参数说明:
| 参数 | 类型 | 说明 |
|---|---|---|
| user_agent | bool | UA设置 |
| case_sensitive | string | 路径大小写敏感设置 值:auto(默认)/no/yes |
| limit_crawler_scope | bool | 将抓取限制为仅包含地址和子目录 值:true(默认)/false |
| excluded_paths | list | 排除路径 |
HTTP 设置
认证方式
支持Basic,Digest,NTLM和Kerberos(仅Windows)的认证方式
Method:PATCH
URL: /api/v1/targets/{target_id}/configuration发送参数说明:
| 参数 | 类型 | 说明 |
|---|---|---|
| enabled | bool | false/true |
| username | string | 用户名 |
| password | string | 密码 |
Data:
{"authentication":{"enabled":true,"username":"administrator","password":"P@ssw0rd"}}客户端证书设置
Method:PATCH
URL: /api/v1/targets/{target_id}/configuration发送参数说明:
| 参数 | 说明 |
|---|---|
| client_certificate_password | 客户端证书密码 |
| client_certificate_url | 客户端证书URL |
Demo:
{"client_certificate_password":"","client_certificate_url":null}代理设置
Method:PATCH
URL: /api/v1/targets/{target_id}/configuration发送参数说明:
| 参数 | 说明 |
|---|---|
| enabled | false/true |
| protocol | 协议 默认http |
| address | 代理ip地址 |
| port | 代理端口 |
| username | 用户名 (可选参数) |
| password | 密码 (可选参数) |
{"proxy":{"enabled":true,"protocol":"http","address":"127.0.0.1","port":2333,"username":"test","password":"P@ssw0rd"}}高级设置
Method:PATCH
URL: /api/v1/targets/{target_id}/configuration参数说明:
| 参数 | 说明 |
|---|---|
| technologies | 检测技术 |
| custom_headers | 自定义cookie |
| debug | 是否开启Debug |
| issue_tracker_id | 问题追踪器ID |
| excluded_hours_id | 排除的工作时间id |
Demo:
{"technologies":["PHP"],"custom_headers":[],"custom_cookies":[],"debug":false,"issue_tracker_id":"","excluded_hours_id":""}Scan 扫描
添加扫描
Method:POST
URL: /api/v1/scansData:
{
"target_id":"64496c9e-b340-4227-90d4-ac43e78d4a0d",
"profile_id":"11111111-1111-1111-1111-111111111112",
"schedule":
{"disable":false,
"start_date":null,
"time_sensitive":false
}
}发送参数说明:
| 参数 | 类型 | 说明 |
|---|---|---|
| profile_id | string | 扫描类型 |
| ui_session_i | string | 可不传 |
| incremental | bool | 增加的? |
| schedule | json | 扫描时间设置(默认即时) |
| report_template_id | string | 扫描报告类型(可不传) |
| target_id | string | 目标id |
AWVS13扫描类型profile_id对照表:
| 类型 | 值 | |
|---|---|---|
| Full Scan | 11111111-1111-1111-1111-111111111111 | 完全扫描 |
| High Risk Vulnerabilities | 11111111-1111-1111-1111-111111111112 | 高风险漏洞 |
| Cross-site Scripting Vulnerabilities | 11111111-1111-1111-1111-111111111116 | XSS漏洞 |
| SQL Injection Vulnerabilities | 11111111-1111-1111-1111-111111111113 | SQL注入漏洞 |
| Weak Passwords | 11111111-1111-1111-1111-111111111115 | 弱口令检测 |
| Crawl Only | 11111111-1111-1111-1111-111111111117 | Crawl Only |
| Malware Scan | 11111111-1111-1111-1111-111111111120 | 恶意软件扫描 |
请求头Data:
{"profile_id":"11111111-1111-1111-1111-111111111111","ui_session_id":"968396ab3b580c3abb4e56a6a7ace40b","incremental":false,"schedule":{"disable":false,"start_date":null,"time_sensitive":false},"report_template_id":"11111111-1111-1111-1111-111111111111","target_id":"f054de11-783a-4978-9186-3346f167c471"}返回值:
{
"profile_id": "11111111-1111-1111-1111-111111111111",
"schedule": {
"disable": false,
"start_date": null,
"time_sensitive": false,
"triggerable": false
},
"target_id": "f054de11-783a-4978-9186-3346f167c471",
"incremental": false,
"max_scan_time": 0,
"report_template_id": "11111111-1111-1111-1111-111111111111",
"ui_session_id": null
}获取目标的扫描id
Method:GET
URL: /api/v1/scans/{target_id}返回参数说明:
| 参数 | 说明 |
|---|---|
| criticality | 危险程度 |
| current_session | 当前会话 |
| start_date | 开始扫描时间 |
| status | 扫描状态 |
| threat | 威胁性 |
| incremental | 额外的? |
| manual_intervention | 人工干预 |
| max_scan_time | 最大扫描时间 |
| next_run | 下一轮 |
| profile_id | 扫描类型 |
| profile_name | 扫描类型名称 |
| report_template_id | 扫描报告模板id |
| scan_id | 扫描id |
| schedule | 时间表 |
| target | 目标相关的信息 |
| target_id | 目标id |
详细返回信息:
{
"criticality": 10,
"current_session": {
"event_level": 0,
"progress": 0,
"scan_session_id": "25a99e14-6301-41b8-8ed8-3bec989936d5",
"severity_counts": {
"high": 0,
"info": 0,
"low": 0,
"medium": 0
},
"start_date": "2020-04-14T04:22:15.311735+00:00",
"status": "queued",
"threat": 0
},
"incremental": false,
"manual_intervention": false,
"max_scan_time": 0,
"next_run": null,
"profile_id": "11111111-1111-1111-1111-111111111111",
"profile_name": "Full Scan",
"report_template_id": null,
"scan_id": "f20b7ffe-a8e4-4b1a-912d-7b319e02bddc",
"schedule": {
"disable": false,
"history_limit": null,
"recurrence": null,
"start_date": null,
"time_sensitive": false,
"triggerable": false
},
"target": {
"address": "https://www.baidu.com",
"criticality": 10,
"description": "Baidu",
"type": "default"
},
"target_id": "f054de11-783a-4978-9186-3346f167c471"
}评论区网友补充:api/v1/targets/target_id 获取 scan_id
删除扫描
Method:DELETE
URL: /api/v1/scans/{scan_id}删除成功,返回024的状态码
获取所有扫描状态
Method:GET
URL: /api/v1/scans?l={count}请求参数说明:
| 参数 | 类型 | 说明 |
|---|---|---|
| l | int | 每页的显示结果 |
返回参数说明:
| 参数 | 说明 |
|---|---|
| pagination | 分页 |
| criticality | 危险程度 |
| current_session | 当前会话 |
| event_level | 事件等级 |
| progress | 新增 |
| scan_session_id | 扫描会话id |
| severity_counts | 漏洞等级分布 |
| start_date | 开始时间 |
| status | 扫描状态 |
| threat | 威胁等级 |
| incremental | 增加的? |
| max_scan_time | 最大扫描时间 |
| next_run | 下一轮 |
| profile_id | 扫描类型 |
| schedule | 时间表 |
| target | 目标 |
| target_id | 目标id |
实际返回信息:
{
"pagination": {
"count": 2,
"cursor_hash": "ad1285c42f54aace75b8c6704ab6d933",
"cursors": [
null
],
"sort": null
},
"scans": [
{
"criticality": 10,
"current_session": {
"event_level": 1,
"progress": 0,
"scan_session_id": "7c3a3d93-1c30-4584-9fd8-3db84e6c1b8e",
"severity_counts": {
"high": 0,
"info": 0,
"low": 0,
"medium": 0
},
"start_date": "2020-04-14T08:12:34.383931+00:00",
"status": "processing",
"threat": 0
},
"incremental": false,
"max_scan_time": 0,
"next_run": null,
"profile_id": "11111111-1111-1111-1111-111111111111",
"profile_name": "Full Scan",
"report_template_id": null,
"scan_id": "e6b32641-7576-4a5e-8e1e-640b2256e681",
"schedule": {
"disable": false,
"history_limit": null,
"recurrence": null,
"start_date": null,
"time_sensitive": false,
"triggerable": false
},
"target": {
"address": "https://www.baidu.com",
"criticality": 10,
"description": "Baidu",
"type": "default"
},
"target_id": "f054de11-783a-4978-9186-3346f167c471"
},
{
"criticality": 10,
"current_session": {
"acusensor": true,
"event_level": 1,
"progress": 100,
"scan_session_id": "21124419-2a02-458e-82bf-fabab3462ddc",
"severity_counts": {
"high": 45,
"info": 26,
"low": 10,
"medium": 66
},
"start_date": "2020-04-13T10:17:09.880580+00:00",
"status": "completed",
"threat": 3
},
"incremental": false,
"max_scan_time": 0,
"next_run": null,
"profile_id": "11111111-1111-1111-1111-111111111111",
"profile_name": "Full Scan",
"report_template_id": null,
"scan_id": "506a2238-aaf2-487a-884b-b152fedffb10",
"schedule": {
"disable": false,
"history_limit": null,
"recurrence": null,
"start_date": null,
"time_sensitive": false,
"triggerable": false
},
"target": {
"address": "http://testphp.vulnweb.com/",
"criticality": 10,
"description": "AWVS\u6d4b\u8bd5\u9776\u573a",
"type": "default"
},
"target_id": "7b70e73f-bad0-4531-99a8-69d916ed7e66"
}
]
}获取单个扫描状态
Method:GET
URL: /api/v1/scans/{scan_id}返回参数说明:
| 参数 | 说明 |
|---|---|
| criticality | 危险程度 |
| current_session | 当前会话 |
| acusensor | 是否启用acu传感器 |
| event_level | 时间级别 |
| progress | 新增数 |
| scan_session_id | 扫描会话id |
| severity_counts | 漏洞等级分布 |
| start_date | 开始扫描时间 |
| status | 扫描状态 |
| threat | 威胁 |
| incremental | 增加的? |
| manual_intervention | 人工干预 |
| max_scan_time | 最大扫描时间 |
| next_run | 下一轮 |
| profile_id | 扫描类型id |
| profile_name | 扫描类型名称 |
| report_template_id | 报告模板id |
| scan_id | 扫描id |
| schedule | 时间表 |
| target | 目标 |
| target_id | 目标id |
实际返回信息:
{
"criticality": 10,
"current_session": {
"acusensor": true,
"event_level": 1,
"progress": 100,
"scan_session_id": "21124419-2a02-458e-82bf-fabab3462ddc",
"severity_counts": {
"high": 45,
"info": 26,
"low": 10,
"medium": 66
},
"start_date": "2020-04-13T10:17:09.880580+00:00",
"status": "completed",
"threat": 3
},
"incremental": false,
"manual_intervention": false,
"max_scan_time": 0,
"next_run": null,
"profile_id": "11111111-1111-1111-1111-111111111111",
"profile_name": "Full Scan",
"report_template_id": null,
"scan_id": "506a2238-aaf2-487a-884b-b152fedffb10",
"schedule": {
"disable": false,
"history_limit": null,
"recurrence": null,
"start_date": null,
"time_sensitive": false,
"triggerable": false
},
"target": {
"address": "http://testphp.vulnweb.com/",
"criticality": 10,
"description": "AWVS\u6d4b\u8bd5\u9776\u573a",
"type": "default"
},
"target_id": "7b70e73f-bad0-4531-99a8-69d916ed7e66"
}评论区网友补充:通过
api/v1/targets/{target_id}可以获取最后一次 scan_id
单个扫描概况信息
Method:GET
URL: /api/v1/scans/{scan_id}/results/{scan_session_id}/statistics返回参数信息:
| 参数 | 说明 |
|---|---|
| scanning_app | 正在扫描的app |
| vulns | 漏洞 |
| name | 漏洞名称 |
| time | 漏洞发现时间 |
| vuln_id | 漏洞id |
| severity | 严重程度 |
| target_info | 目标信息 |
| host | 目标域名 |
| target_id | 目标id |
| status | 扫描状态 |
| duration | 持续时间 |
| messages | 消息 |
| data | 消息data |
| kind | 消息类别 |
| time | 消息时间 |
| level | 消息级别 |
| target_info | 目标信息 |
| progress | 新增 |
| web_scan_status | Web扫描状态 |
| locations | 位置 |
| request_count | 请求数 |
| avg_response_time | 平均响应时间 |
| max_response_time | 最大响应时间 |
| status_statistics | 状态统计 |
| operationStatsByRun | 运行状态 |
| locationStatsByRequest | 按请求列出的位置统计信息 |
| locationStatsByAvgDuration | 按平均持续时间列出的位置统计 |
| locationStatsByTotalDuration | 按总持续时间列出的位置统计 |
| operationStatsByTotalDuration | 按总持续时间列出的操作状态 |
| host | hosts id |
| aborted | 中止 |
| target_info | 目标信息 |
| os | 操作系统 |
| server | Web Server |
| responsive | 有反应的 |
| aborted_reason | 中止理由 |
| external_hosts | 其他相关域名 |
| web_scan_status | web扫描状态 |
| locations | 位置 |
| request_count | 请求数 |
| avg_response_time | 平均响应时间 |
| max_response_time | 最长响应时间 |
| is_starting_host | 是否开始扫描 |
| status | 扫描状态 |
| abort_requested | 请求终止 |
| start_date | 开始日期 |
| end_date | 结束日期 |
| end_deadline | 截止日期 |
实际返回信息:
{
"scanning_app": {
"wvs": {
"main": {
"vulns": [
{
"name": "Subresource Integrity (SRI) not implemented",
"time": "2020-04-14T08:13:15.849264+00:00",
"vuln_id": "2287002727030458306",
"severity": 0,
"target_info": {
"host": "www.baidu.com",
"target_id": "f054de11-783a-4978-9186-3346f167c471"
}
},
{
"name": "Cookie(s) without Secure flag set",
"time": "2020-04-14T08:13:15.780950+00:00",
"vuln_id": "2287002726451644352",
"severity": 1,
"target_info": {
"host": "www.baidu.com",
"target_id": "f054de11-783a-4978-9186-3346f167c471"
}
},
{
"name": "Cookie(s) without Secure flag set",
"time": "2020-04-14T08:13:15.713772+00:00",
"vuln_id": "2287002725897996222",
"severity": 1,
"target_info": {
"host": "www.baidu.com",
"target_id": "f054de11-783a-4978-9186-3346f167c471"
}
},
{
"name": "Cookie(s) without Secure flag set",
"time": "2020-04-14T08:13:15.649198+00:00",
"vuln_id": "2287002725335959484",
"severity": 1,
"target_info": {
"host": "www.baidu.com",
"target_id": "f054de11-783a-4978-9186-3346f167c471"
}
},
{
"name": "Cookie(s) without HttpOnly flag set",
"time": "2020-04-14T08:13:15.581567+00:00",
"vuln_id": "2287002724773922746",
"severity": 1,
"target_info": {
"host": "www.baidu.com",
"target_id": "f054de11-783a-4978-9186-3346f167c471"
}
}
],
"status": "finished",
"duration": 39,
"messages": [
{
"data": "",
"kind": "antivirus_not_found",
"time": "2020-04-14T08:12:38.058683+00:00",
"level": 1,
"target_info": null
},
{
"data": "",
"kind": "scanning",
"time": "2020-04-14T08:12:37.842455+00:00",
"level": -1,
"target_info": {
"host": "www.baidu.com",
"target_id": "f054de11-783a-4978-9186-3346f167c471"
}
}
],
"progress": 100,
"web_scan_status": {
"locations": 17,
"request_count": 2033,
"avg_response_time": 11,
"max_response_time": 2085
},
"status_statistics": {
"operationStatsByRun": [
{
"number_of_runs": 9,
"operation_name": "/location/forceful_browsing.js",
"total_duration": 722,
"average_duration": 80
},
{
"number_of_runs": 9,
"operation_name": "/location/reverse_proxy_path_traversal.js",
"total_duration": 40,
"average_duration": 4
},
{
"number_of_runs": 9,
"operation_name": "/location/ruby_source_code_disclosure.js",
"total_duration": 96,
"average_duration": 10
},
{
"number_of_runs": 9,
"operation_name": "/location/sap_b2b_lfi.js",
"total_duration": 10,
"average_duration": 1
},
{
"number_of_runs": 9,
"operation_name": "/location/nodejs_source_code_disclosure.js",
"total_duration": 66,
"average_duration": 7
},
{
"number_of_runs": 9,
"operation_name": "/location/jquery_file_upload_rce.js",
"total_duration": 548,
"average_duration": 60
},
{
"number_of_runs": 9,
"operation_name": "/location/laravel_log_viewer_lfd.js",
"total_duration": 36,
"average_duration": 4
},
{
"number_of_runs": 9,
"operation_name": "/location/nodejs_path_traversal_CVE-2017-14849.js",
"total_duration": 50,
"average_duration": 5
},
{
"number_of_runs": 9,
"operation_name": "/location/npm_debug_log.js",
"total_duration": 33,
"average_duration": 3
},
{
"number_of_runs": 9,
"operation_name": "/location/python_source_code_disclosure.js",
"total_duration": 184,
"average_duration": 20
}
],
"locationStatsByRequest": [
{
"location_name": "https://www.baidu.com/",
"total_duration": 24732,
"average_duration": 27,
"number_of_requests": 912
},
{
"location_name": "https://www.baidu.com/s",
"total_duration": 19702,
"average_duration": 98,
"number_of_requests": 200
},
{
"location_name": "https://www.baidu.com/baidu.html",
"total_duration": 21521,
"average_duration": 29,
"number_of_requests": 727
},
{
"location_name": "https://www.baidu.com/ups/submit/",
"total_duration": 1080,
"average_duration": 38,
"number_of_requests": 28
},
{
"location_name": "https://www.baidu.com/ups/submit/addtips/",
"total_duration": 2772,
"average_duration": 24,
"number_of_requests": 112
},
{
"location_name": "https://www.baidu.com/cache/",
"total_duration": 1286,
"average_duration": 51,
"number_of_requests": 25
},
{
"location_name": "https://www.baidu.com/cache/sethelp/",
"total_duration": 952,
"average_duration": 35,
"number_of_requests": 27
},
{
"location_name": "https://www.baidu.com/cache/sethelp/index.html",
"total_duration": 44,
"average_duration": 22,
"number_of_requests": 2
}
],
"locationStatsByAvgDuration": [
{
"location_name": "https://www.baidu.com/",
"total_duration": 24732,
"average_duration": 27,
"number_of_requests": 912
},
{
"location_name": "https://www.baidu.com/s",
"total_duration": 19702,
"average_duration": 98,
"number_of_requests": 200
},
{
"location_name": "https://www.baidu.com/baidu.html",
"total_duration": 21521,
"average_duration": 29,
"number_of_requests": 727
},
{
"location_name": "https://www.baidu.com/ups/submit/",
"total_duration": 1080,
"average_duration": 38,
"number_of_requests": 28
},
{
"location_name": "https://www.baidu.com/ups/submit/addtips/",
"total_duration": 2772,
"average_duration": 24,
"number_of_requests": 112
},
{
"location_name": "https://www.baidu.com/cache/",
"total_duration": 1286,
"average_duration": 51,
"number_of_requests": 25
},
{
"location_name": "https://www.baidu.com/cache/sethelp/",
"total_duration": 952,
"average_duration": 35,
"number_of_requests": 27
},
{
"location_name": "https://www.baidu.com/cache/sethelp/index.html",
"total_duration": 44,
"average_duration": 22,
"number_of_requests": 2
}
],
"locationStatsByTotalDuration": [
{
"location_name": "https://www.baidu.com/",
"total_duration": 24732,
"average_duration": 27,
"number_of_requests": 912
},
{
"location_name": "https://www.baidu.com/s",
"total_duration": 19702,
"average_duration": 98,
"number_of_requests": 200
},
{
"location_name": "https://www.baidu.com/baidu.html",
"total_duration": 21521,
"average_duration": 29,
"number_of_requests": 727
},
{
"location_name": "https://www.baidu.com/ups/submit/",
"total_duration": 1080,
"average_duration": 38,
"number_of_requests": 28
},
{
"location_name": "https://www.baidu.com/ups/submit/addtips/",
"total_duration": 2772,
"average_duration": 24,
"number_of_requests": 112
},
{
"location_name": "https://www.baidu.com/cache/",
"total_duration": 1286,
"average_duration": 51,
"number_of_requests": 25
},
{
"location_name": "https://www.baidu.com/cache/sethelp/",
"total_duration": 952,
"average_duration": 35,
"number_of_requests": 27
},
{
"location_name": "https://www.baidu.com/cache/sethelp/index.html",
"total_duration": 44,
"average_duration": 22,
"number_of_requests": 2
}
],
"operationStatsByTotalDuration": [
{
"number_of_runs": 1,
"operation_name": "/Scripts/PerServer/Apache_Solr_Exposed.script",
"total_duration": 18373,
"average_duration": 18373
},
{
"number_of_runs": 1,
"operation_name": "/target/cassandra_open.js",
"total_duration": 29964,
"average_duration": 29964
},
{
"number_of_runs": 1,
"operation_name": "/target/weblogic_rce_CVE-2018-3245.js",
"total_duration": 29964,
"average_duration": 29964
},
{
"number_of_runs": 1,
"operation_name": "/target/redis_open.js",
"total_duration": 29958,
"average_duration": 29958
},
{
"number_of_runs": 1,
"operation_name": "/Scripts/PerServer/Hadoop_Cluster_Web_Interface.script",
"total_duration": 27959,
"average_duration": 27959
},
{
"number_of_runs": 1,
"operation_name": "/target/fastcgi_unauth.js",
"total_duration": 29971,
"average_duration": 29971
},
{
"number_of_runs": 1,
"operation_name": "/target/memcached_open.js",
"total_duration": 29958,
"average_duration": 29958
},
{
"number_of_runs": 1,
"operation_name": "/target/apache_spark_audit.js",
"total_duration": 20232,
"average_duration": 20232
},
{
"number_of_runs": 1,
"operation_name": "/Scripts/PerServer/JMX_RMI_service.script",
"total_duration": 20964,
"average_duration": 20964
},
{
"number_of_runs": 1,
"operation_name": "/target/docker_engine_API_exposed.js",
"total_duration": 19986,
"average_duration": 19986
}
]
}
},
"hosts": {
"f054de11-783a-4978-9186-3346f167c471": {
"host": "www.baidu.com",
"aborted": null,
"target_info": {
"os": "Unknown",
"server": "BWS/1.1",
"responsive": true
},
"aborted_reason": null,
"external_hosts": [
"https://dss0.bdstatic.com",
"https://ss1.bdstatic.com",
"https://sp1.baidu.com",
"https://ss1.baidu.com",
"https://ss0.baidu.com",
"https://ss3.baidu.com",
"https://ss2.baidu.com",
"https://dss1.bdstatic.com",
"https://passport.baidu.com",
"https://wappass.baidu.com",
"https://passport.bdimg.com",
"https://nsclick.baidu.com",
"https://sp0.baidu.com",
"https://sp2.baidu.com",
"http://www.baidu.com",
"https://voice.baidu.com",
"http://news.baidu.com",
"https://www.hao123.com",
"http://map.baidu.com",
"http://v.baidu.com",
"http://tieba.baidu.com",
"http://xueshu.baidu.com",
"https://home.baidu.com",
"http://ir.baidu.com",
"http://e.baidu.com",
"https://help.baidu.com",
"http://www.beian.gov.cn",
"http://zhidao.baidu.com",
"http://music.taihe.com",
"http://image.baidu.com",
"http://wenku.baidu.com",
"https://dss1.baidu.com",
"https://dss3.bdstatic.com",
"https://cambrian-images.cdn.bcebos.com",
"https://dss0.baidu.com",
"https://dss2.bdstatic.com",
"https://timg01.bdimg.com",
"https://img1.bdstatic.com",
"https://img0.bdstatic.com",
"https://imgstat.baidu.com",
"https://timgsa.baidu.com",
"https://img2.bdstatic.com",
"https://image.baidu.com",
"http://home.baidu.com",
"http://jianyi.baidu.com",
"https://ss2.bdstatic.com"
],
"web_scan_status": {
"locations": 17,
"request_count": 1899,
"avg_response_time": 10,
"max_response_time": 1496
},
"is_starting_host": true
}
},
"status": "aborted",
"abort_requested": true,
"start_date": "2020-04-14T08:12:34.369124+00:00",
"end_date": "2020-04-14T08:13:18.287592+00:00",
"end_deadline": "2020-04-16T08:12:34.365524+00:00",
"event_level": 1
}
},
"status": "aborted",
"severity_counts": {
"high": 0,
"medium": 2,
"low": 26,
"info": 3
}
}单个扫描漏洞结果
Method:GET
URL: /api/v1/scans/{scan_id}/results/{scan_session_id}/vulnerabilities?l={count}&s=severity:desc请求接口信息:
| 接口 | 说明 |
|---|---|
| l | 显示数量 |
返回接口信息:
| 接口 | 说明 |
|---|---|
| vulnerabilities | 脆弱性 |
| affects_detail | 影响详细信息 |
| affects_url | 影响URL |
| confidence | 信心 |
| criticality | 危险程度 |
| last_seen | last_seen |
| loc_id | loc id |
| status | 状态 |
| tags | 漏洞标签 |
| target_id | 目标id |
| vt_id | vt_id |
| vt_name | 漏洞名称 |
| vuln_id | 漏洞类别id |
| pagination | 分页 |
返回详细信息:
{
"vulnerabilities": [
{
"affects_detail": "searchFor",
"affects_url": "http://testphp.vulnweb.com/search.php",
"confidence": 100,
"criticality": 10,
"last_seen": null,
"loc_id": 129,
"severity": 3,
"status": "open",
"tags": [
"verified",
"CWE-79",
"xss"
],
"target_id": "7b70e73f-bad0-4531-99a8-69d916ed7e66",
"vt_id": "7a2fa5a4-7125-1062-0651-ed5219f05809",
"vt_name": "Cross site scripting",
"vuln_id": "2286341152976143767"
},
{
"affects_detail": "uaddress",
"affects_url": "http://testphp.vulnweb.com/secured/newuser.php",
"confidence": 100,
"criticality": 10,
"last_seen": null,
"loc_id": 317,
"severity": 3,
"status": "open",
"tags": [
"verified",
"CWE-79",
"xss"
],
"target_id": "7b70e73f-bad0-4531-99a8-69d916ed7e66",
"vt_id": "7a2fa5a4-7125-1062-0651-ed5219f05809",
"vt_name": "Cross site scripting",
"vuln_id": "2286341419087955369"
},
{
"affects_detail": "ucc",
"affects_url": "http://testphp.vulnweb.com/secured/newuser.php",
"confidence": 100,
"criticality": 10,
"last_seen": null,
"loc_id": 317,
"severity": 3,
"status": "open",
"tags": [
"verified",
"CWE-79",
"xss"
],
"target_id": "7b70e73f-bad0-4531-99a8-69d916ed7e66",
"vt_id": "7a2fa5a4-7125-1062-0651-ed5219f05809",
"vt_name": "Cross site scripting",
"vuln_id": "2286341419515774379"
},
{
"affects_detail": "uemail",
"affects_url": "http://testphp.vulnweb.com/secured/newuser.php",
"confidence": 100,
"criticality": 10,
"last_seen": null,
"loc_id": 317,
"severity": 3,
"status": "open",
"tags": [
"verified",
"CWE-79",
"xss"
],
"target_id": "7b70e73f-bad0-4531-99a8-69d916ed7e66",
"vt_id": "7a2fa5a4-7125-1062-0651-ed5219f05809",
"vt_name": "Cross site scripting",
"vuln_id": "2286341419935204781"
}
],
"pagination": {
"count": 147,
"cursor_hash": "212c913db3a92b9f3eb3a0a44d611667",
"cursors": [
null,
"5",
"10"
],
"sort": "severity:desc"
}
}获取当前扫描单个漏洞信息
Method: GET
URL: /api/v1/scans/{scan_id}/results/{scan_session_id}/vulnerabilities/{vuln_id}返回参数说明:
| 参数 | 说明 |
|---|---|
| affects_detail | 影响细节 |
| affects_url | 影响URL |
| confidence | 准确率 |
| criticality | 危险程度 |
| cvss2 | cvss2信息 |
| cvss3 | cvss3信息 |
| cvss_score | cvss评分 |
| description | 漏洞描述 |
| highlights | 高亮 |
| impact | 影响 |
| loc_id | loc id |
| long_description | 更多描述 |
| references | 参考链接来源 |
| request | 请求头信息 |
| response_info | 返回头信息 |
| severity | 漏洞等级(0-3) |
| source | 使用的脚本链接 |
| status | 状态 |
| tags | 标签 |
| target_id | 目标id |
| vt_id | 漏洞id |
| vt_name | 漏洞名称 |
| vuln_id | 漏洞所属类型id |
返回详细信息:
{
"affects_detail": "searchFor",
"affects_url": "http://testphp.vulnweb.com/search.php",
"confidence": 100,
"criticality": 10,
"cvss2": "AV:N/AC:L/Au:N/C:P/I:P/A:N",
"cvss3": "CVSS:3.0/AV:N/AC:L/PR:N/UI:N/S:U/C:N/I:L/A:N",
"cvss_score": 5.3,
"description": "Cross-site Scripting (XSS) refers to client-side code injection attack wherein an attacker can execute malicious scripts into a legitimate website or web application. XSS occurs when a web application makes use of unvalidated or unencoded user input within the output it generates.",
"details": " URL encoded POST input <strong><span class=\"bb-dark\">searchFor</span></strong> was set to <strong><span class=\"bb-dark\">the'"()&%<acx><ScRiPt >Dta8(9300)</ScRiPt></span></strong><br/> ",
"highlights": [
{
"index": 2289,
"length": 6,
"in": "body"
},
{
"index": 2297,
"length": 10,
"in": "body"
}
],
"impact": "Malicious JavaScript has access to all the same objects as the rest of the web page, including access to cookies and local storage, which are often used to store session tokens. If an attacker can obtain a user's session cookie, they can then impersonate that user.<br/><br/>\n\nFurthermore, JavaScript can read and make arbitrary modifications to the contents of a page being displayed to a user. Therefore, XSS in conjunction with some clever social engineering opens up a lot of possibilities for an attacker.",
"loc_id": 129,
"long_description": "In order for a Cross-site scripting (XSS) attack to take place, an attacker does not directly target a victim. Instead, an attacker exploits a vulnerability in a web application visited by a victim, where the web application is used to deliver the malicious JavaScript. The victim's browser is not able to distinguish between malicious and legitimate JavaScript, and therefore, executes the attacker's malicious payload.<br/><br/> Since cross-site scripting (XSS) is user input which is interpreted as code. In order to prevent XSS, secure input handling is necessary. The two fundamental methods of handling untrusted user input are <strong>encoding</strong> and <strong>validation</strong>.<br/><br/> <ul> <li><strong>Encoding</strong> - Escapes user input so that browsers interpret it as <strong>data</strong>, not as code</li> <li><strong>Validation</strong> - Filters user input so that browsers interpret it as code without malicious commands</li> </ul><br/> Encoding and validation are two different techniques to preventing cross-site scripting (XSS). Deciding which should be used highly depends on the <strong>context</strong> within which the untrusted user input is being inserted.<br/><br/> The following are two examples of the most common cross-site scripting (XSS) contexts.<br/> <pre> <!-- HTML element --> <div><strong><span class=\"bb-dark\">userInput</span></strong></div> <!-- HTML attribute --> <input value="<strong><span class=\"bb-dark\">userInput</strong></span>"> </pre> The method for preventing cross-site (XSS) scripting in the two examples above is different. In the first example, where user input is inserted in an HTML element, HTML encoding is the correct way to prevent XSS. However, in the second example, where user input is inserted in an HTML attribute, validation (in this case, filtering out <code>'</code> and <code>"</code>)is the appropriate prevention method.<br/> <pre> <!-- Application code --> <input value="<strong><span class=\"bb-dark\">userInput</span></strong>"> <!-- Malicious string --> "><script>...</script><input value=" <!-- Resulting code --> <input value="<strong><span class=\"bb-dark\">"><script>...</script><input value="</strong></span>"> </pre> In <strong>most</strong> of the time, encoding should be performed whenever user input is included in a page, however, as with the above example, in some cases, encoding has to be replaced by or complemented with validation.<br/><br/> It's important to remember that secure input handling has to take into account which context of a page the user input is inserted into.",
"recommendation": "Apply context-dependent encoding and/or validation to user input rendered on a page",
"references": [
{
"href": "https://www.acunetix.com/websitesecurity/cross-site-scripting/",
"rel": "Cross-site Scripting (XSS) Attack - Acunetix"
},
{
"href": "https://www.acunetix.com/websitesecurity/xss/",
"rel": "Types of XSS - Acunetix"
},
{
"href": "https://www.owasp.org/index.php/XSS_Filter_Evasion_Cheat_Sheet",
"rel": "XSS Filter Evasion Cheat Sheet"
},
{
"href": "https://excess-xss.com/",
"rel": "Excess XSS, a comprehensive tutorial on cross-site scripting"
},
{
"href": "https://en.wikipedia.org/wiki/Cross-site_scripting ",
"rel": "Cross site scripting"
}
],
"request": "POST /search.php?test=query HTTP/1.1\r\nContent-Type: application/x-www-form-urlencoded\r\nReferer: http://testphp.vulnweb.com/\r\nAccept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8\r\nAccept-Encoding: gzip,deflate\r\nContent-Length: 70\r\nHost: testphp.vulnweb.com\r\nUser-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/73.0.3683.103 Safari/537.36\r\nConnection: Keep-alive\r\n\r\ngoButton=go&searchFor=the'\"()%26%25<acx><ScRiPt%20>Dta8(9300)</ScRiPt>",
"response_info": true,
"severity": 3,
"source": "/Scripts/PerScheme/XSS.script",
"status": "open",
"tags": [
"verified",
"CWE-79",
"xss"
],
"target_id": "7b70e73f-bad0-4531-99a8-69d916ed7e66",
"vt_id": "7a2fa5a4-7125-1062-0651-ed5219f05809",
"vt_name": "Cross site scripting",
"vuln_id": "2286341152976143767"
}Vulnerabilities 脆弱性
获取所有漏洞信息
Method:GET
URL: /api/v1/vulnerabilities?l=20&q=status:openl: 分页查询
status: 默认为open
| 值 | 说明 |
|---|---|
| open | 公开 |
| fixed | 已修复 |
| ignored | 已忽略 |
| false_positive | 误报 |
| !open | 不公开 |
返回参数说明:
| 参数 | 说明 |
|---|---|
| pagination | 页码信息 |
| vulnerabilities | 漏洞信息 |
实际返回信息:
{
"vulnerabilities": [
{
"affects_detail": "searchFor",
"affects_url": "http://testphp.vulnweb.com/search.php",
"confidence": 100,
"continuous": false,
"criticality": 10,
"issue_id": null,
"last_seen": "2020-04-13T10:18:50.070007+00:00",
"severity": 3,
"status": "open",
"tags": [
"verified",
"CWE-79",
"xss"
],
"target_description": "AWVS\u6d4b\u8bd5\u9776\u573a",
"target_id": "7b70e73f-bad0-4531-99a8-69d916ed7e66",
"vt_id": "7a2fa5a4-7125-1062-0651-ed5219f05809",
"vt_name": "Cross site scripting",
"vuln_id": "2286341152959366550"
},
{
"affects_detail": "uaddress",
"affects_url": "http://testphp.vulnweb.com/secured/newuser.php",
"confidence": 100,
"continuous": false,
"criticality": 10,
"issue_id": null,
"last_seen": "2020-04-13T10:19:21.793149+00:00",
"severity": 3,
"status": "open",
"tags": [
"verified",
"CWE-79",
"xss"
],
"target_description": "AWVS\u6d4b\u8bd5\u9776\u573a",
"target_id": "7b70e73f-bad0-4531-99a8-69d916ed7e66",
"vt_id": "7a2fa5a4-7125-1062-0651-ed5219f05809",
"vt_name": "Cross site scripting",
"vuln_id": "2286341419071178152"
},
{
"affects_detail": "ucc",
"affects_url": "http://testphp.vulnweb.com/secured/newuser.php",
"confidence": 100,
"continuous": false,
"criticality": 10,
"issue_id": null,
"last_seen": "2020-04-13T10:19:21.843254+00:00",
"severity": 3,
"status": "open",
"tags": [
"verified",
"CWE-79",
"xss"
],
"target_description": "AWVS\u6d4b\u8bd5\u9776\u573a",
"target_id": "7b70e73f-bad0-4531-99a8-69d916ed7e66",
"vt_id": "7a2fa5a4-7125-1062-0651-ed5219f05809",
"vt_name": "Cross site scripting",
"vuln_id": "2286341419490608554"
}
],
"pagination": {
"count": 188,
"cursor_hash": "94d01e070606634a4efab4c82395e7ce",
"cursors": [
null,
"WzEwLCAzLCAiQ3Jvc3Mgc2l0ZSBzY3JpcHRpbmciLCAyMjg2MzQxNDE5OTE4NDI3NTY0XQ==",
"WzEwLCAzLCAiQ3Jvc3Mgc2l0ZSBzY3JpcHRpbmciLCAyMjg2MzQxNDIxMTUxNTUyOTQ2XQ=="
],
"sort": null
}
}条件筛选漏洞信息
Method:GET
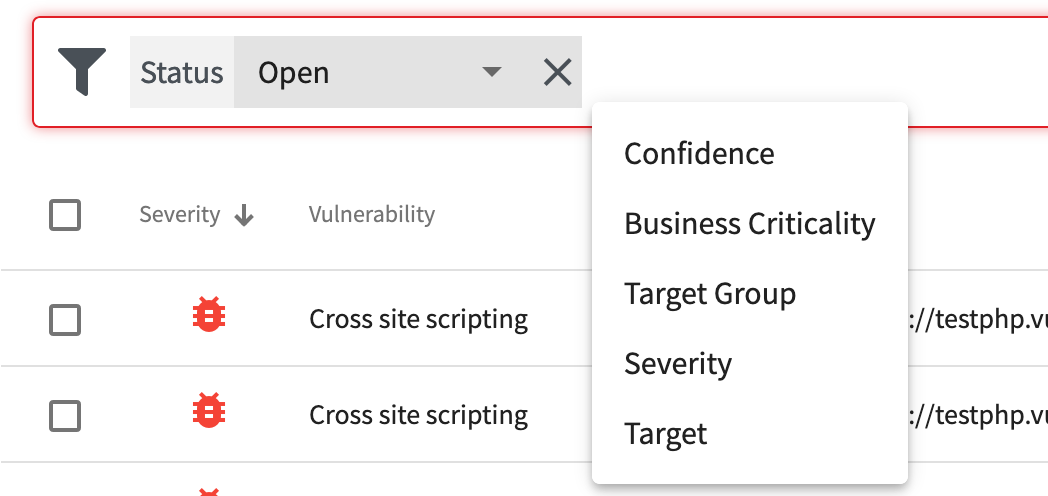
URL: /api/v1/vulnerabilities?q=severity:{int};criticality:{int};status:{string};cvss_score:{logic expression};cvss_score:{logic expression};target_id:{target_id};group_id:{group_id}这里实际上就是对应AWVS的这一块的过滤筛选器,如果接口有误差就参考过滤器自己抓包即可:
获取单个漏洞信息
说明: 此处的vuln_id 应是根据本模块中获取全部漏洞信息中得到的vuln_id, 不能将scans模块得到的vuln_id传入,否则无法获取到漏洞信息。
Method:GET
URL: api/v1/vulnerabilities/{vuln_id}实际返回信息:
{
"affects_detail": "searchFor",
"affects_url": "http://testphp.vulnweb.com/search.php",
"confidence": 100,
"continuous": false,
"criticality": 10,
"cvss2": "AV:N/AC:L/Au:N/C:P/I:P/A:N",
"cvss3": "CVSS:3.0/AV:N/AC:L/PR:N/UI:N/S:U/C:N/I:L/A:N",
"cvss_score": 5.3,
"description": "Cross-site Scripting (XSS) refers to client-side code injection attack wherein an attacker can execute malicious scripts into a legitimate website or web application. XSS occurs when a web application makes use of unvalidated or unencoded user input within the output it generates.",
"details": " URL encoded POST input <strong><span class=\"bb-dark\">searchFor</span></strong> was set to <strong><span class=\"bb-dark\">the'"()&%<acx><ScRiPt >Dta8(9300)</ScRiPt></span></strong><br/> ",
"highlights": [
{
"index": 2289,
"length": 6,
"in": "body"
},
{
"index": 2297,
"length": 10,
"in": "body"
}
],
"impact": "Malicious JavaScript has access to all the same objects as the rest of the web page, including access to cookies and local storage, which are often used to store session tokens. If an attacker can obtain a user's session cookie, they can then impersonate that user.<br/><br/>\n\nFurthermore, JavaScript can read and make arbitrary modifications to the contents of a page being displayed to a user. Therefore, XSS in conjunction with some clever social engineering opens up a lot of possibilities for an attacker.",
"issue_id": null,
"last_seen": "2020-04-13T10:18:50.070007+00:00",
"loc_id": null,
"long_description": "In order for a Cross-site scripting (XSS) attack to take place, an attacker does not directly target a victim. Instead, an attacker exploits a vulnerability in a web application visited by a victim, where the web application is used to deliver the malicious JavaScript. The victim's browser is not able to distinguish between malicious and legitimate JavaScript, and therefore, executes the attacker's malicious payload.<br/><br/> Since cross-site scripting (XSS) is user input which is interpreted as code. In order to prevent XSS, secure input handling is necessary. The two fundamental methods of handling untrusted user input are <strong>encoding</strong> and <strong>validation</strong>.<br/><br/> <ul> <li><strong>Encoding</strong> - Escapes user input so that browsers interpret it as <strong>data</strong>, not as code</li> <li><strong>Validation</strong> - Filters user input so that browsers interpret it as code without malicious commands</li> </ul><br/> Encoding and validation are two different techniques to preventing cross-site scripting (XSS). Deciding which should be used highly depends on the <strong>context</strong> within which the untrusted user input is being inserted.<br/><br/> The following are two examples of the most common cross-site scripting (XSS) contexts.<br/> <pre> <!-- HTML element --> <div><strong><span class=\"bb-dark\">userInput</span></strong></div> <!-- HTML attribute --> <input value="<strong><span class=\"bb-dark\">userInput</strong></span>"> </pre> The method for preventing cross-site (XSS) scripting in the two examples above is different. In the first example, where user input is inserted in an HTML element, HTML encoding is the correct way to prevent XSS. However, in the second example, where user input is inserted in an HTML attribute, validation (in this case, filtering out <code>'</code> and <code>"</code>)is the appropriate prevention method.<br/> <pre> <!-- Application code --> <input value="<strong><span class=\"bb-dark\">userInput</span></strong>"> <!-- Malicious string --> "><script>...</script><input value=" <!-- Resulting code --> <input value="<strong><span class=\"bb-dark\">"><script>...</script><input value="</strong></span>"> </pre> In <strong>most</strong> of the time, encoding should be performed whenever user input is included in a page, however, as with the above example, in some cases, encoding has to be replaced by or complemented with validation.<br/><br/> It's important to remember that secure input handling has to take into account which context of a page the user input is inserted into.",
"recommendation": "Apply context-dependent encoding and/or validation to user input rendered on a page",
"references": [
{
"href": "https://www.acunetix.com/websitesecurity/cross-site-scripting/",
"rel": "Cross-site Scripting (XSS) Attack - Acunetix"
},
{
"href": "https://www.acunetix.com/websitesecurity/xss/",
"rel": "Types of XSS - Acunetix"
},
{
"href": "https://www.owasp.org/index.php/XSS_Filter_Evasion_Cheat_Sheet",
"rel": "XSS Filter Evasion Cheat Sheet"
},
{
"href": "https://excess-xss.com/",
"rel": "Excess XSS, a comprehensive tutorial on cross-site scripting"
},
{
"href": "https://en.wikipedia.org/wiki/Cross-site_scripting ",
"rel": "Cross site scripting"
}
],
"request": "POST /search.php?test=query HTTP/1.1\r\nContent-Type: application/x-www-form-urlencoded\r\nReferer: http://testphp.vulnweb.com/\r\nAccept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8\r\nAccept-Encoding: gzip,deflate\r\nContent-Length: 70\r\nHost: testphp.vulnweb.com\r\nUser-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/73.0.3683.103 Safari/537.36\r\nConnection: Keep-alive\r\n\r\ngoButton=go&searchFor=the'\"()%26%25<acx><ScRiPt%20>Dta8(9300)</ScRiPt>",
"response_info": true,
"severity": 3,
"source": "/Scripts/PerScheme/XSS.script",
"status": "open",
"tags": [
"verified",
"CWE-79",
"xss"
],
"target_description": "AWVS\u6d4b\u8bd5\u9776\u573a",
"target_id": "7b70e73f-bad0-4531-99a8-69d916ed7e66",
"vt_id": "7a2fa5a4-7125-1062-0651-ed5219f05809",
"vt_name": "Cross site scripting",
"vuln_id": "2286341152959366550"
}Reports 报告
获取所有扫描报告
Method:GET
URL: /api/v1/reports?l={count}?l={count}返回参数说明:
| 参数 | 说明 |
|---|---|
| pagination | 分页 |
| reports | 报告 |
| download | 下载链接[html, pdf] |
| generation_date | 生成日期 |
| report_id | 报告ID |
| source | 来源 |
| status | 状态 |
| template_id | 模板id |
| template_name | 模板名称 |
实际返回信息:
{
"pagination": {
"count": 1,
"cursor_hash": "ad1285c42f54aace75b8c6704ab6d933",
"cursors": [
null
],
"sort": null
},
"reports": [
{
"download": [
"/api/v1/reports/download/d934580e86291e1b0f725892e0c0296ae4c26db14a346de4766e104d3fc5b4796326ad115e9597c1f4ee8dd5-2234-4d91-a93b-f5039242b1ab.html",
"/api/v1/reports/download/ccd08287711e89344cfd66b90e53c89e03a9396b73e1f672ca1c6bbd22a715043f6f08ac5e9597c1f4ee8dd5-2234-4d91-a93b-f5039242b1ab.pdf"
],
"generation_date": "2020-04-13T04:30:38.044204+00:00",
"report_id": "f4ee8dd5-2234-4d91-a93b-f5039242b1ab",
"source": {
"list_type": "scan_result",
"description": "http://testphp.vulnweb.com/;AWVS\u9776\u573a",
"id_list": [
"df99f637-fe77-403d-866e-ba1d36286bb9"
]
},
"status": "completed",
"template_id": "11111111-1111-1111-1111-111111111115",
"template_name": "Affected Items",
"template_type": 0
}
]
}AWVS13扫描类型template_id对照表:
| 类型 | 值 |
|---|---|
| Affected Items | 11111111-1111-1111-1111-111111111115 |
| Developer | 11111111-1111-1111-1111-111111111111 |
| Executive Summary | 11111111-1111-1111-1111-111111111113 |
| Quick | 11111111-1111-1111-1111-111111111112 |
| CWE 2011 | 11111111-1111-1111-1111-111111111116 |
| HIPAA | 11111111-1111-1111-1111-111111111114 |
| ISO 27001 | 11111111-1111-1111-1111-111111111117 |
| NIST SP800 53 | 11111111-1111-1111-1111-111111111118 |
| OWASP Top 10 2013 | 11111111-1111-1111-1111-111111111119 |
| OWASP Top 10 2017 | 11111111-1111-1111-1111-111111111125 |
| PCI DSS 3.2 | 11111111-1111-1111-1111-111111111120 |
| Sarbanes Oxley | 11111111-1111-1111-1111-111111111121 |
| STIG DISA | 11111111-1111-1111-1111-111111111122 |
| WASC Threat Classification | 11111111-1111-1111-1111-111111111123 |
删除单个报告
Method:DELETE
URL: /api/v1/reports/{report_id}总结
再参考了前辈h4rdy的 AWVS11 的 API 后,国光根据前辈的文档全部都一个个验证尝试了,发现 AWVS13 的 API 变动不大,期间只有几个小功能没有复现验证成功,有的通过抓包解决了,有的现在依然没有解决(AWVS13 上传登录序列这一块),如果有解决方法的朋友欢迎评论分享解决方法,目前评论区已经指出了几个问题了,大家也可以参考下评论区的解决方法。
参考资料
支持一下
本文可能实际上也没有啥技术含量,但是写起来还是比较浪费时间的,在这个喧嚣浮躁的时代,个人博客越来越没有人看了,写博客感觉一直是用爱发电的状态。如果你恰巧财力雄厚,感觉本文对你有所帮助的话,可以考虑打赏一下本文,用以维持高昂的服务器运营费用(域名费用、服务器费用、CDN费用等)
微信
 |
支付宝
 |
没想到文章加入打赏列表没几天 就有热心网友打赏了 于是国光我用 Bootstrap 重写了一个页面用以感谢支持我的朋友,详情请看 打赏列表 | 国光